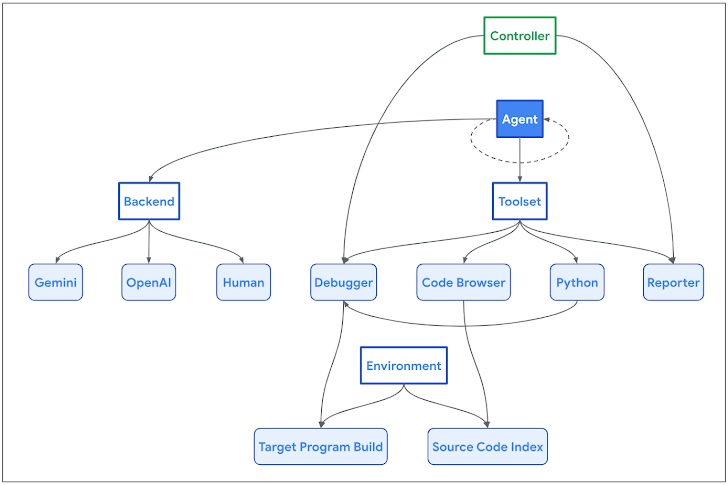
Apple Intelligence
Apple Intelligence : On Device Processing
Edge-AI Privacy Innovation / Security Blueprint from Apple WWDC24 Conference
Apple WWDC24 Keynote has some amazing GENAI Edge Innovation and brilliant engineering science on display which they talked about how on-device models that can outsource to Apple’s servers. Most notable is their approach to features that don’t work with an on-device model.

Apple WWDC24 Keynote : Apple Intelligence Reference YouTube video at 1h14m43s
Apple-intelligence
When you make a request, Apple Intelligence analysis whether it can be processed on device. If it needs greater computational capacity, it can draw on Private Cloud Compute, and send only the data that’s relevant to your task to be processed on Apple Silicon servers.
Your data is never stored or made accessible to Apple. It’s used exclusively to fulfill your request. And just like your iPhone, independent experts can inspect the code that runs on the servers to verify this privacy promise.
In fact, Private Cloud Compute cryptographically ensures your iPhone, iPad, and Mac will refuse to talk to a server unless its software has been publicly logged for inspection.
This sets a brand new standard on Privacy and AI